This article provides insights to a forensic case study showing procedures normally associated with this type of investigation and steps taken by the investigators, including challenges that can arise during legal proceedings.
Abstract
During a recent internal investigation, a forensic analyst was asked to examine a corporate laptop for evidence of theft, misappropriation, and/or other misconduct including but not limited to taking any proprietary information outside of the organization: in particular, any information that may have been copied, emailed, and/or transferred. During the review, evidence was found that two USB devices were connected to the laptop and proprietary information was copied prior to the user’s separation with the company (Figure 1). This article provides insights to a forensic case study showing procedures normally associated with this type of investigation and steps taken by the investigators, including challenges that can arise during legal proceedings.
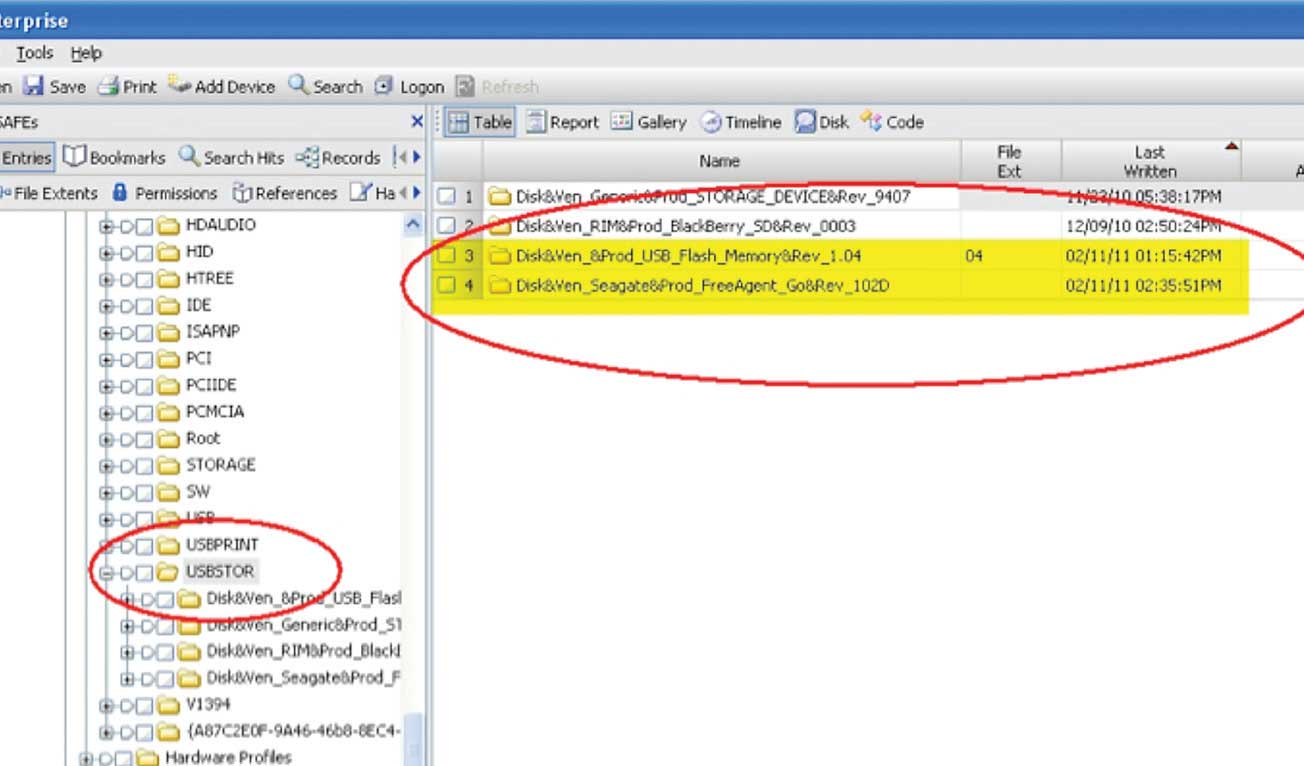
Figure 1 – The Windows system registry reveals entries of two USB devices connected to the laptop on 02/11/11.
Methodology
In an effort to determine whether any files were copied to these USB devices, procedures commonly associated with this type of investigation were carefully followed. These included a review of link and log files entries, recovery of link files from unallocated space, review of event logs, analysis of Windows registry artifacts, review of recently accessed files, etc. As part of standard methodology, the forensic analysis included the review of the disk activity following the introduction of these USB devices. A time-line analysis, focusing on Last Accessed, Entry Modified, Last Written, and File Created date stamps of the files following the connection of the USB devices, was performed.
Findings
During the review, it was noticed that for about 991 files the Last Accessed date stamps were modified sequentially in a 19-second interval (see footnote below) consistent with files copying (see Figure 2). However, due to the fact that other types of activities could have possibly changed the Last Accessed dates on these files, it was important to rule out other possibilities through experimentation.
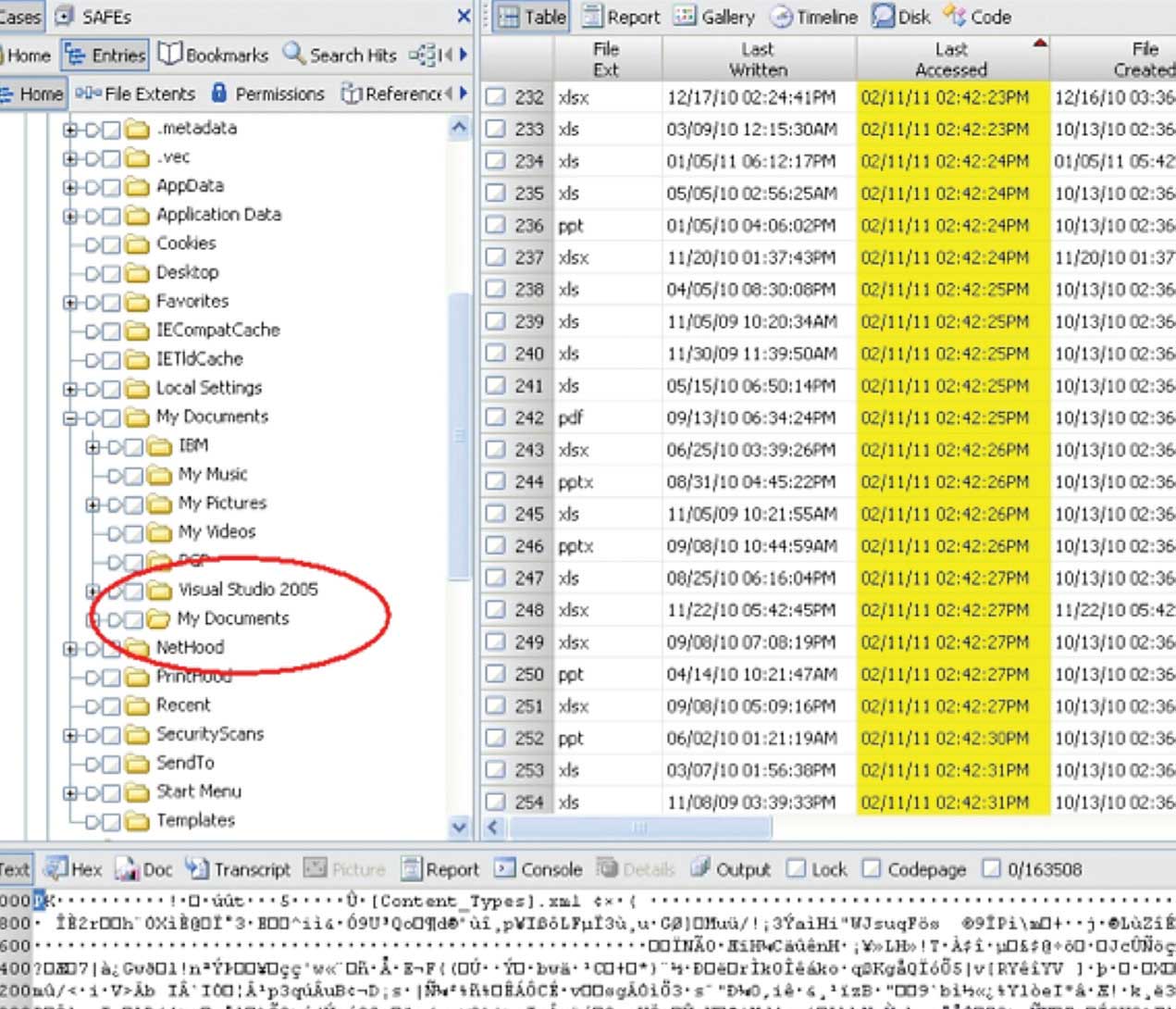
Figure 2 – It was not possible to capture all 99 files in a single exhibit; therefore, this exhibit shows 23 files out of 99 within the My Documents folder where the Last Accessed date stamps were sequentially modified in an 8-second interval. This figure represents a subset of the entire dataset and is provided as an example for the readers of what was observed by the examiner.
Experimentation:
First, due to the number of files (99), size of data (99MB) and the time window interval (19 sec), it was necessary to attempt to replicate the file copying hypothesis. To start, a forensic image of the laptop was restored and installed into the original laptop. Then a generic flash drive was connected to the computer and successfully replicated the files copying by selecting the 99 files in question and timing the procedure. The experimentation clocked the process at 20 seconds instead of 19; however, considering the original USB device was not used, different results (within a reasonable time frame interval) were expected. Nevertheless, the experimentation effectively reproduced the results. The experimentation had successfully copied 99 files (99MB in size) to an external device within (or very close to) the 19-second interval. Following the file copy experimentation, and after a careful review of the files’ metadata , it was noted that the ‘Last Accessed’ date stamps for such files had been modified as projected, further supporting the forensic findings.
It was concluded that at least 99 files containing proprietary and confidential information were copied to at least one USB device.
Once it was determined that the theory was possible, it was then necessary to rule out any possible scenarios. Continuing with the analysis, the possibility of antivirus software doing a background scanning at the time of the connection was quickly ruled out since a virus engine would have been able to scan 99 files and 99MB of data much faster than 19 seconds. Furthermore, there was familiarity with the corporate antivirus engine deployed through the enterprise. Moreover, an antivirus software would have not done a selective type scanning without user intervention. Meaning that several files were contained within a specific folder and not all files within this folder were modified, only a selective group of these files. Although, this was a far fetch possibility, an attempt was made in trying to replicate the sequence of events by restoring the forensic image of the laptop to a virtual machine in order to boot up the computer and avoid having to do additional image restores. After booting up the virtual machine, files within the folder were accessed to determine if the files would be scanned and/or modified (Last Accessed) in a similar manner. The observation from the experimentation was very different and therefore unable to replicate the original observation.
Second, it was important to rule out if the user had actually opened and reviewed 99 files in an 19 seconds time interval. Although, unlikely, it was still necessary to discard this possibility through experimentation. Therefore, an attempt to open all 99 files was made, and the observation from this experimentation also proved different.
After exhausting all reasonable and possible known scenarios, it was indisputable that the observed activity was consistent with files copying. And consequently, the 'Last Accessed' dates on these 99 files, following the connection of USB device, were indicative of files being copied to the USB device. Therefore, it was concluded that at least 99 files containing proprietary and confidential information were copied to at least one USB device.
Legal Proceedings:
Following the analyst's review, a lawsuit was filed and the defendant was asked to provide the external USB devices connected to the corporate laptop prior to his separation with the company. The defendant was also asked not to alter, delete, and/or modify the data in any way. A preliminary analysis of the USB devices revealed the presence of over 999 (over 1.9GB in size) proprietary and confidential company documents including the 99 files initially identified by the preliminary analysis.
New Evidence:
Further review of the USB devices reveal that the 'Last Accessed' dates of the files identified as proprietary documents and stored in one of the USB devices were also changed in a similar manner than the previous 99 files identified earlier during the investigation. Following the same procedures conducted on the analysis of the laptop, a series of tests were conducted to rule out other possibilities. Upon completion, it was concluded that the files stored in the USB device were probably copied to yet another unknown source, perhaps a computer or another external drive.
The Challenge:
When the new findings were presented, the opposing side immediately challenged the forensic results, and disputed that a known operating system bug had adversely changed the 'Last Accessed' dates on those files, and aggressively argued that his client did not duplicate this information. When his client viewed the content of the drive, files were unfavorably altered, by the simple action of browsing through the external hard drive and not by copying.
Independent Forensic Review:
In order to support the initial findings, the company retained an independent forensic expert to conduct a separate review of the USB mass storage device. The consultant was provided with a forensic image of the USB device and asked to perform an analysis on the evidence to determine if the information (identified as proprietary and confidential) stored in the external device was copied from this device. Independently, it was concluded, that based on the sequentially 'Last Accessed' date stamps, the probability of files being copied was very apparent and the findings were consistent with files copying.
This second opinion was immediately presented to the court, and this strengthened the case for the plaintiff. However, the opposing side maintained their original position and effectively argued that the findings were consistent with a known operating bug, and furthermore, they had successfully replicated the observation. According to the defendant, a known Windows XP 2002 Home Edition flaw causes the operating system to adversely update the ‘Last Accessed’ date properties for all files in a folder, instantly and simultaneously, when the files within that folder are viewed using Windows Explorer. Following opposing side’ arguments, both analysts (corporate and consultant) were asked to carry out additional experimentation to discard the above possibility.
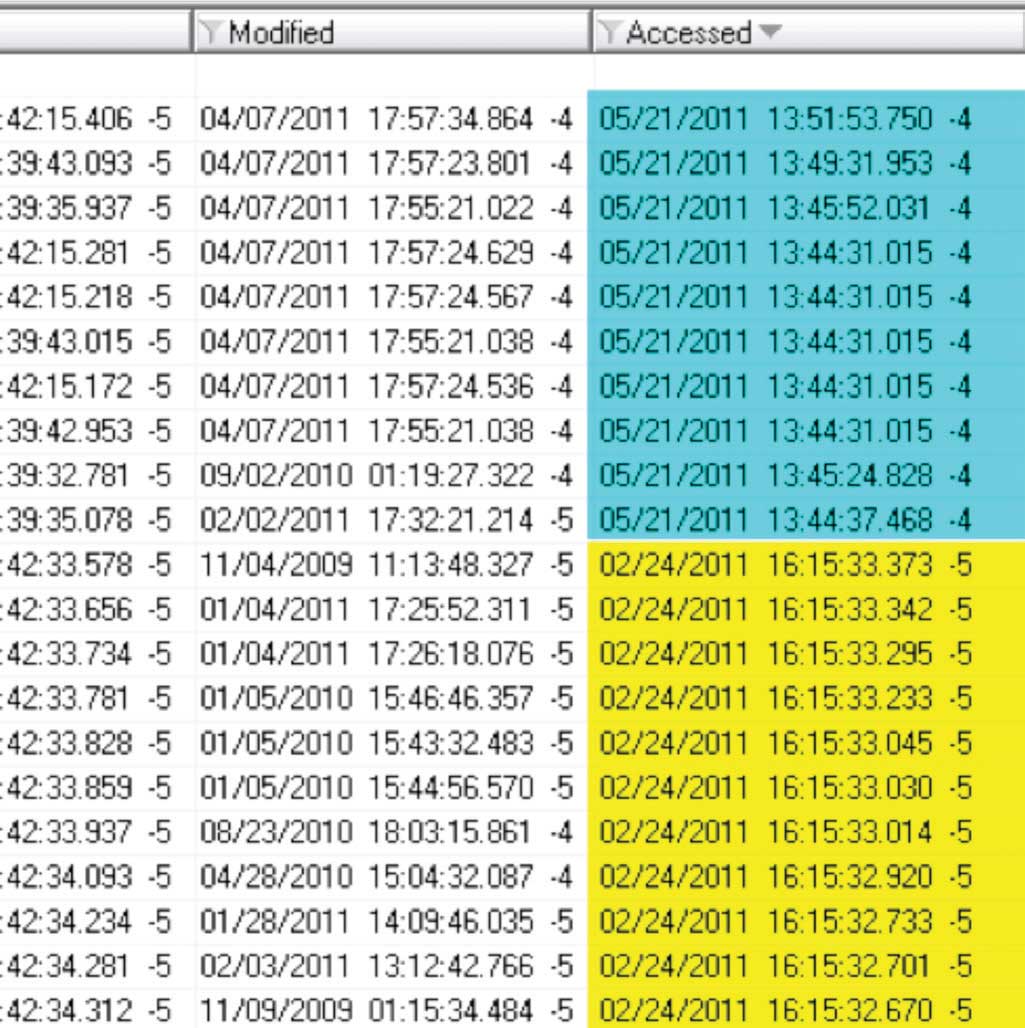
Figure 3 – This figure reveals that not all of the files’ Last Accessed time stamps were modified; some files’ Last Accessed time stamps remained with the 02/24/11 dates.
Additional Experimentation (rule out the bug):
For experimentation purposes, both (a forensic copy of the laptop used to access the files in the mass storage device and a forensic copy of the USB device) images were restored to virtual machines. The USB device was then accessed in a similar manner (following the sequence of events as described by opposing side) and the observation was documented. Both analysts, independently, conducted this experimentation, and both were unable to replicate the findings. After performing several tests with the Windows XP Home 2002 Operating System and a test USB device, the following results were observed:
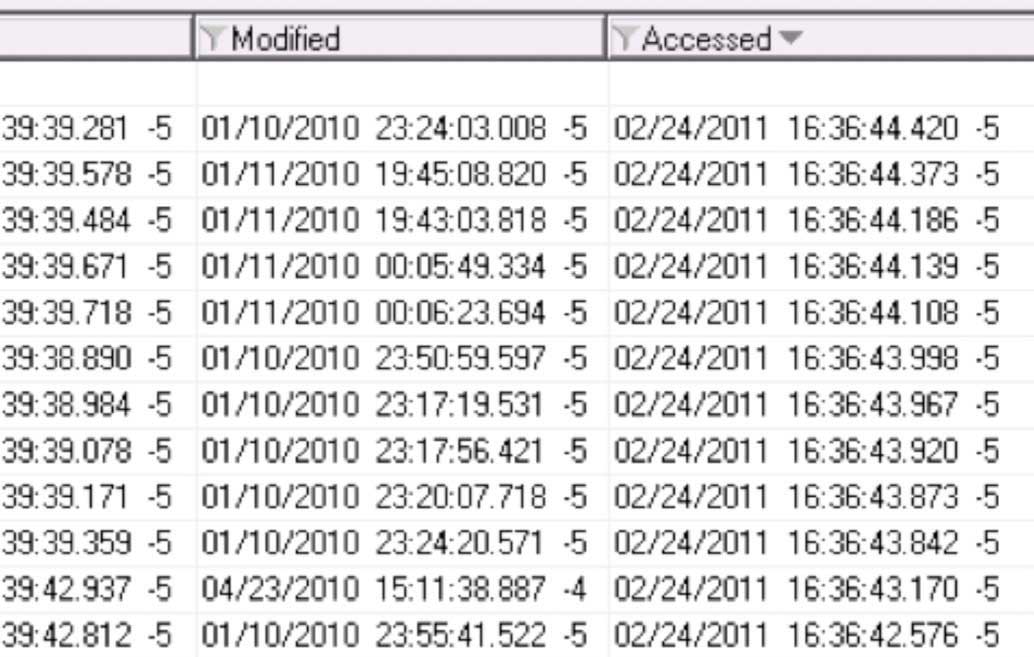
Figure 4 – Last Accessed times of files remain unaltered.
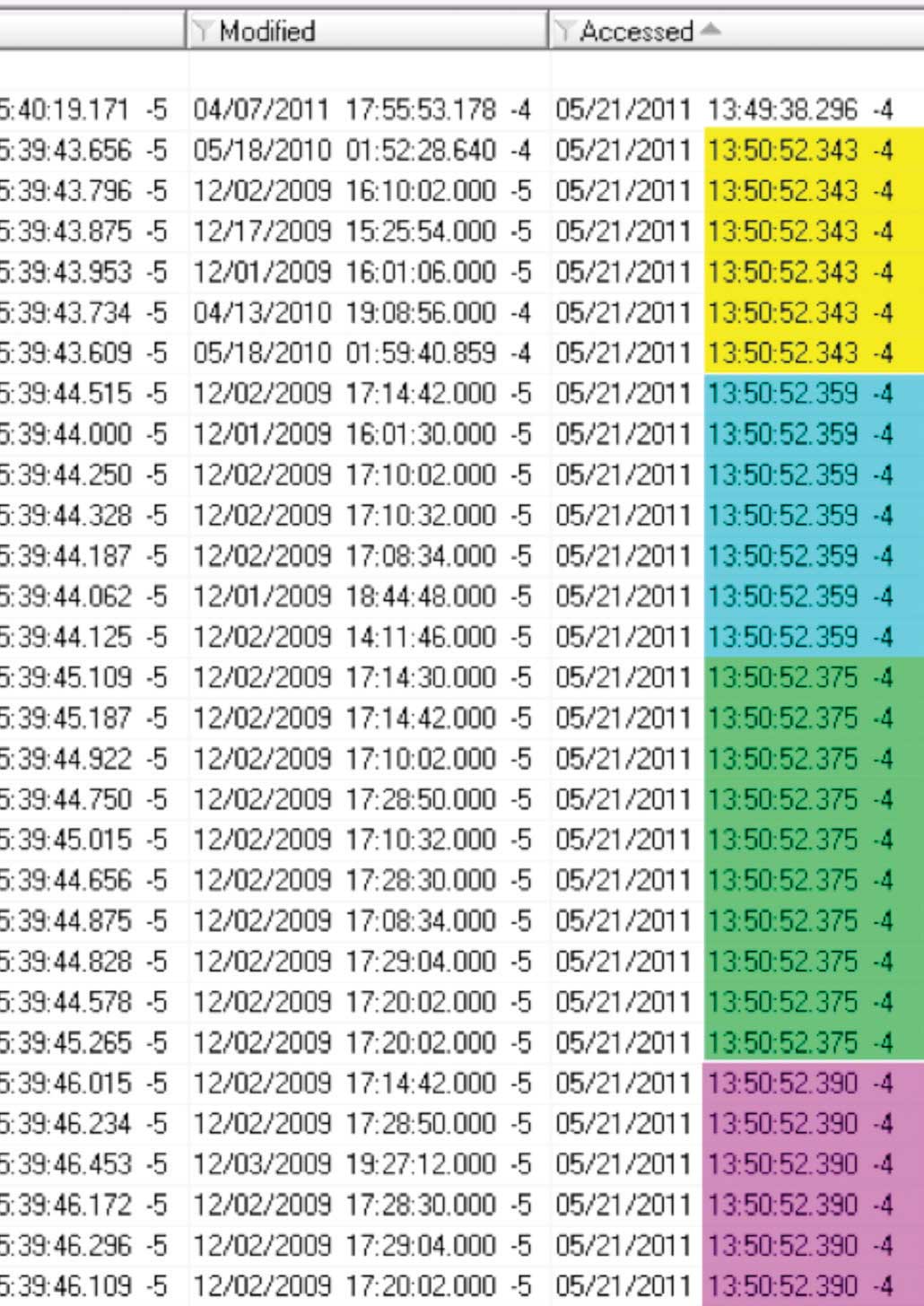
Figure 5 – Last Accessed times were sequentially modified per group of files rather than individually as observed in the original evidence.
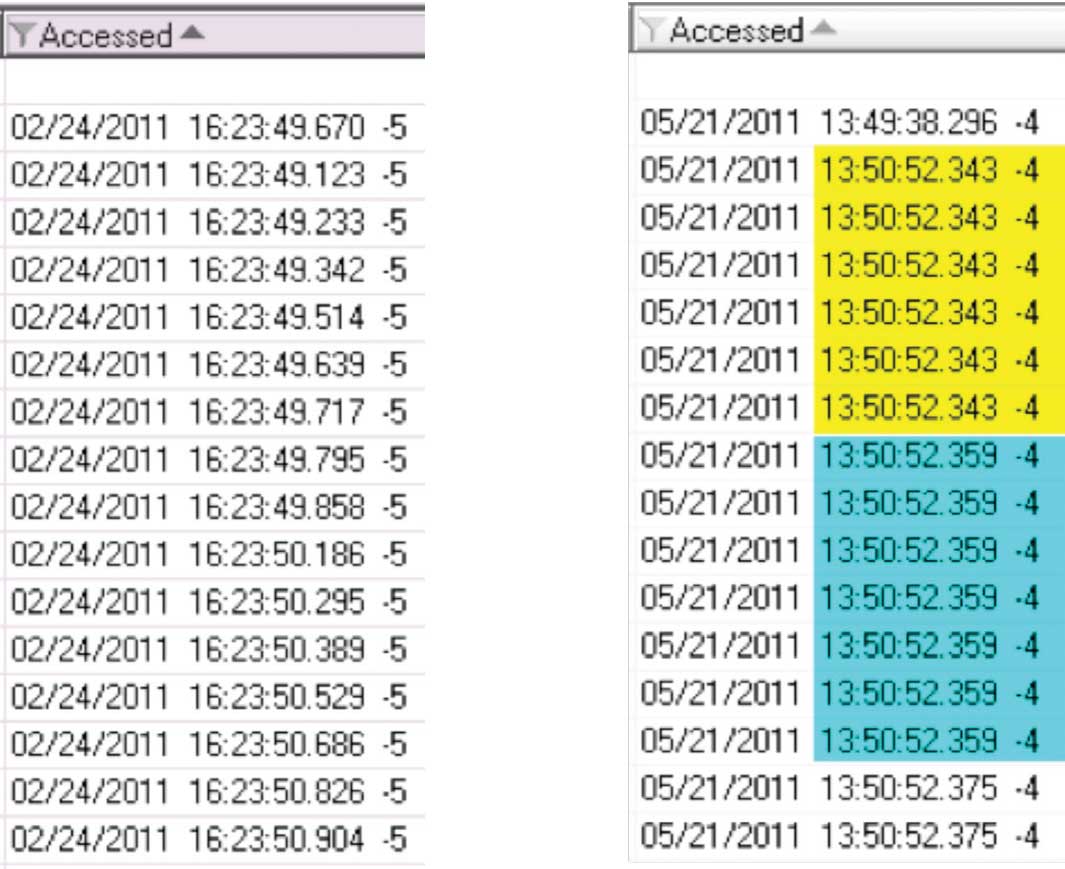
Figure 6 – Comparison of Last Accessed time stamps between Original USB and Test USB devices: Original device does not show grouping while Test device shows grouping.
- 1. All Folders/Directories in the root of test USB device changed their ‘Last Accessed’ time stamps to the time when the test USB device was connected; however, not all of the files ‘Last Accessed’ time stamps were modified as shown by the exhibit below. Also, the time changes occurred in blocks and not sequentially per item, when viewed using forensic software. For the purpose of this experimentation the date was changed to 05/21/11.
- 2. While accessing a folder, it was observed that none of the last ‘Last Accessed’ times of directories or files were modified during the “detail” review performed with Windows Explorer as shown by the following figure.
- 3. Next another folder was accessed with Windows Explorer, and all the files within this folder changed their ‘Last Accessed’ times to 05/21/2011. It is important to note that the ‘Last Accessed’ times were altered sequentially per group (or block) of files rather than per file. The ‘Last Accessed’ times shown, using forensic software; include milliseconds. It is important when making these observations to view the times using forensic software and with the times in milliseconds.
- 4. A comparison of ‘Last Accessed’ time stamps between files from the original USB device and files on the test USB device can be observed below. It is important to note that the Original USB device reveals randomly altered time stamps while the Test USB device reveals times altered sequentially per group.
- 5. In an attempt to replicate the original observation, files were copied to the Test USB device, and the results were very similar to the original observation. Files ‘Last Accessed’ time stamps were randomly altered
Results:
Although the 'Last Accessed' dates on the files stored in the USB device were modified (as opposing side argued), the observation was very different from that of the actual analysis. Files were not modified sequentially per se. Instead files 'Last Accessed' date stamps were modified almost instantly. To conclude, the experimentation could not reproduce the 'Last Accessed' times sequential occurrence observed on the original evidence by just browsing files and folders with Windows Explorer on a Windows XP Home 2002 SP2 system.
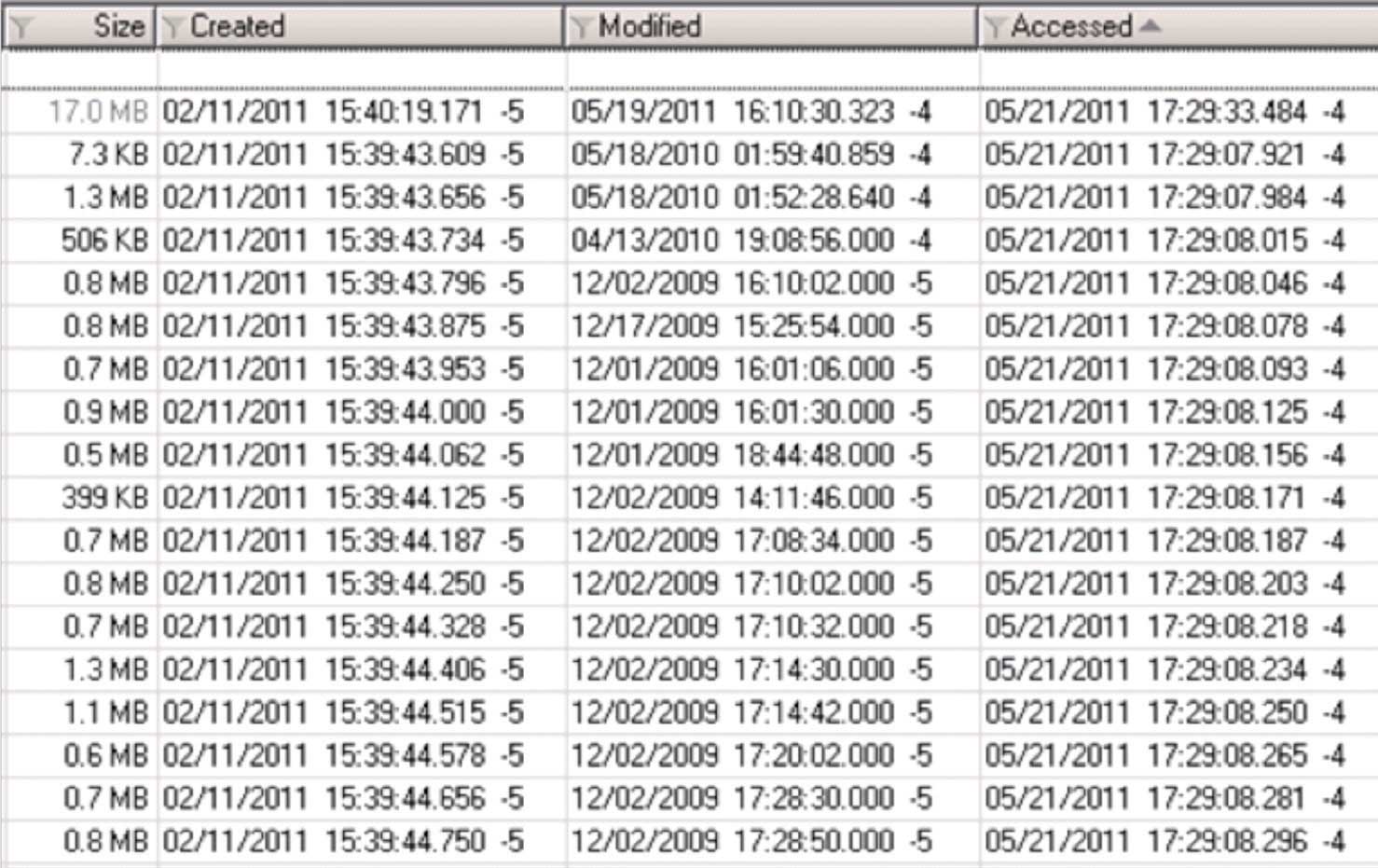
Figure 7 – Last Accessed times were randomly modified as observed in the original evidence.
Back to court (No bugs here):
After completing independent experimentations, the observations from the many tests were presented to the court and opposing side was asked to replicate the events since they had successfully replicated the observation before, the plaintiff’s forensic experts were unable to duplicate the sequence of events. As expected, the opposing side was not able to replicate the events and the case settled successfully on favor of the plaintiff.
Conclusion:
In summary, cases involving the copying of files to mass storage devices exclusively based on 'Last Accessed' dates stamps can be challenging to prove and defend in court. Therefore, to successfully argue a case and/or findings, it is important to rule out all reasonable and possible known scenarios. Although, one cannot rule out all unknown possibilities, ruling out all known possibilities will strengthen one’s case. Both analysts have successfully proven and defended many forensics cases of files being copied to USB devices based exclusively on 'Last Accessed' dates stamps. But until just recently, their findings had never been challenge with such theory. Although both of them knew this theory was far fetch possibility, without strict and detailed documentation of their experimentations and observations, the opposing side could have easily won this matter.
About the Authors:
Ray Yepes is a security professional based in The Woodlands, Texas. With a bachelor’s degree in Computer Science from Sam Houston State University, he is currently working on his Masters of Science in Digital Forensics. He has over 21 years of experience as an IT professional and 16 years as a security analyst and criminal investigations examiner. He has assisted and advised federal, state and local government agencies in criminal investigations, high profile cases, and national security matters since 1995.
Santiago Ayala has over 10 years and 300+ cases of experience in the digital data forensic, information systems technology and cyber security fields. As a Computer Forensic Engineer, Mr. Ayala has assisted in the investigation of high profile civil and criminal cases since 2004. Mr. Ayala has been certified by the International Society of Forensic Computer Examiners as a Certified Computer Examiner (CCE), and by Guidance Software as an EnCase Certified Examiner (EnCE).






